The Digital Premium: Evidence That Buys a Higher Multiple
Oct 24, 2025
Multiple expansion is earned through verified operating systems, not slogans. Buyers test whether revenue is predictable, data is reliable, operations are resilient, security is enforced, and change is repeatable. The objective is to build evidence that survives diligence, reruns cleanly, and travels to the next owner.

1. What buyers actually pay for
-
Predictable demand and pricing: documented rules in CPQ, uplift history, renewal discipline.
-
Reliable data and reporting: single source of truth, KPI lineage, reconciliation to the financials.
-
Resilient execution: cost-to-serve control, inventory hygiene, on-time fulfillment.
-
Security posture: identity and access management, tested incident response.
-
Repeatable change: PMO cadence, hit rate on committed outcomes, archived decisions.
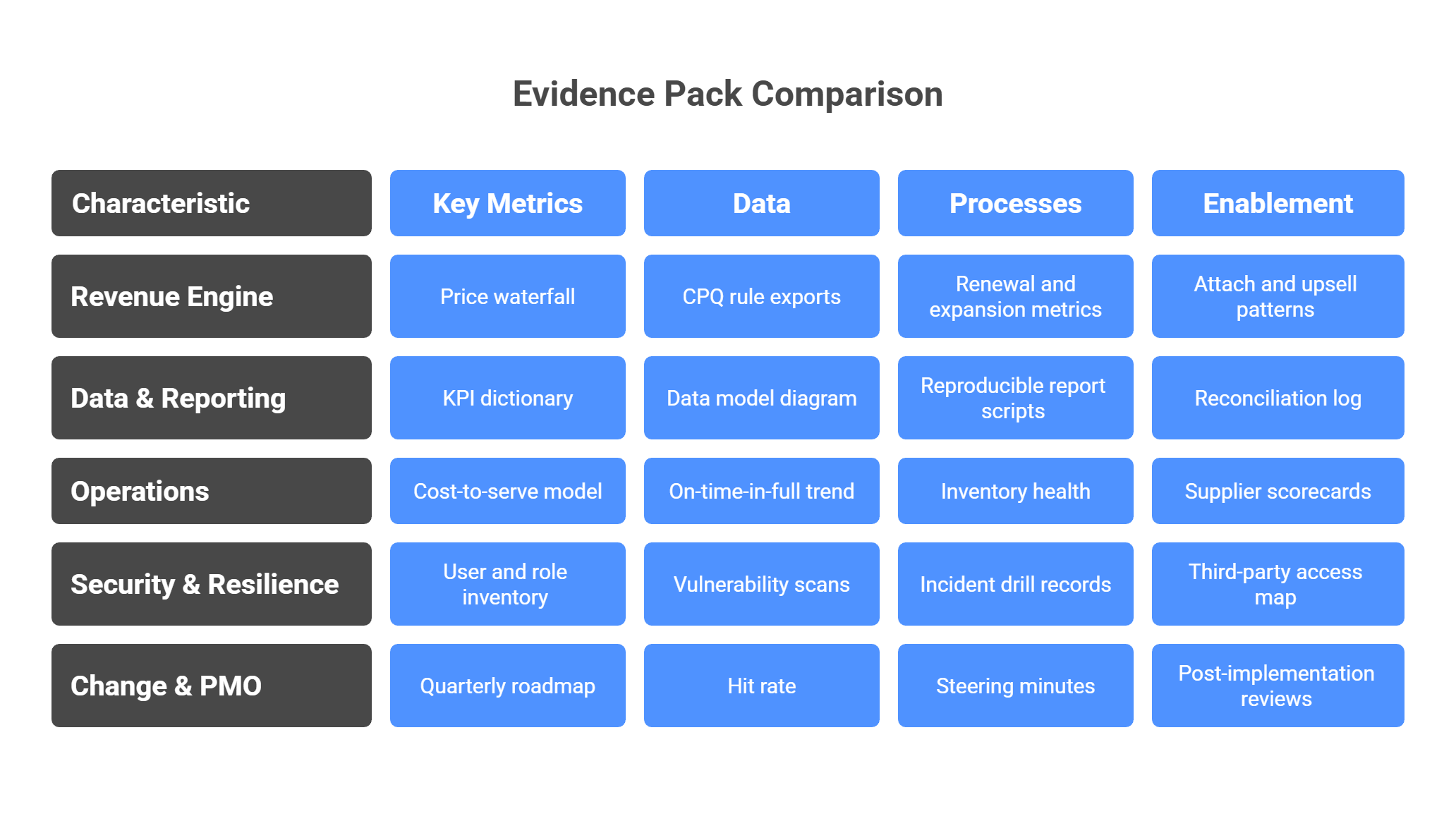
2. Five evidence packs (build these first)
A. Revenue Engine Pack
-
Price waterfall (List → Pocket) with quarterly history.
-
CPQ rule exports: floors, bands, approvals, effective dates.
-
Renewal and expansion metrics: logo retention, net revenue retention, discount compliance.
-
Attach and upsell patterns with talk tracks and enablement notes.
B. Data & Reporting Pack
-
Data model diagram and system inventory.
-
KPI dictionary with lineage to source tables and financial tie-outs.
-
Reproducible report scripts or saved views with timestamps.
-
Reconciliation log showing how each KPI matches the P&L.
C. Operations Pack
-
Cost-to-serve model (drivers, allocation rules, validation notes).
-
On-time-in-full trend, order profile mix, returns profile.
-
Inventory health: turns by family, slow-moving actions, RMA policy and outcomes.
-
Supplier scorecards and routed corrective actions.
D. Security & Resilience Pack
-
User and role inventory, MFA policy coverage, joiner-mover-leaver process.
-
Vulnerability scans and remediation logs with closure dates.
-
Incident drill records with roles, timings, and improvements.
-
Third-party access map and active integrations.
E. Change & PMO Pack
-
Quarterly roadmap with quantifiable outcomes and owners.
-
Hit rate: committed vs delivered, with slippage reasons.
-
Steering minutes, issue logs, and decision registers.
-
Post-implementation reviews with measured effects (revenue, cost, risk).
3. 30-60-90 day plan
Days 1–30: Inventory and truth set
-
Identify systems, reports, and metrics used in board packs.
-
Create a truth set: 12 months of reconciled KPI → financial tie-outs.
-
Freeze ad-hoc report edits; route all changes through a single owner.
-
Deliverables: evidence pack index, KPI dictionary v1, reconciliation workbook.
Days 31–60: Close red gaps
-
Enforce CPQ rules for discount floors and approvals.
-
Fix lineage breaks: remove manual spreadsheet steps, script the pipeline.
-
Run two operational pilots (e.g., MOQ enforcement, returns tightening) and measure effect.
-
Deliverables: CPQ export, scripted reports, pilot memos with before/after charts.
Days 61–90: Package and rehearse
-
Build a data room ready binder for each pack with “how to rerun” notes.
-
Rehearse buyer questions: show artifacts, rerun a KPI live, walk through a variance.
-
Lock a monthly archive cadence so the binder stays current.
-
Deliverables: data room structure, Q&A script, immutable monthly snapshots.
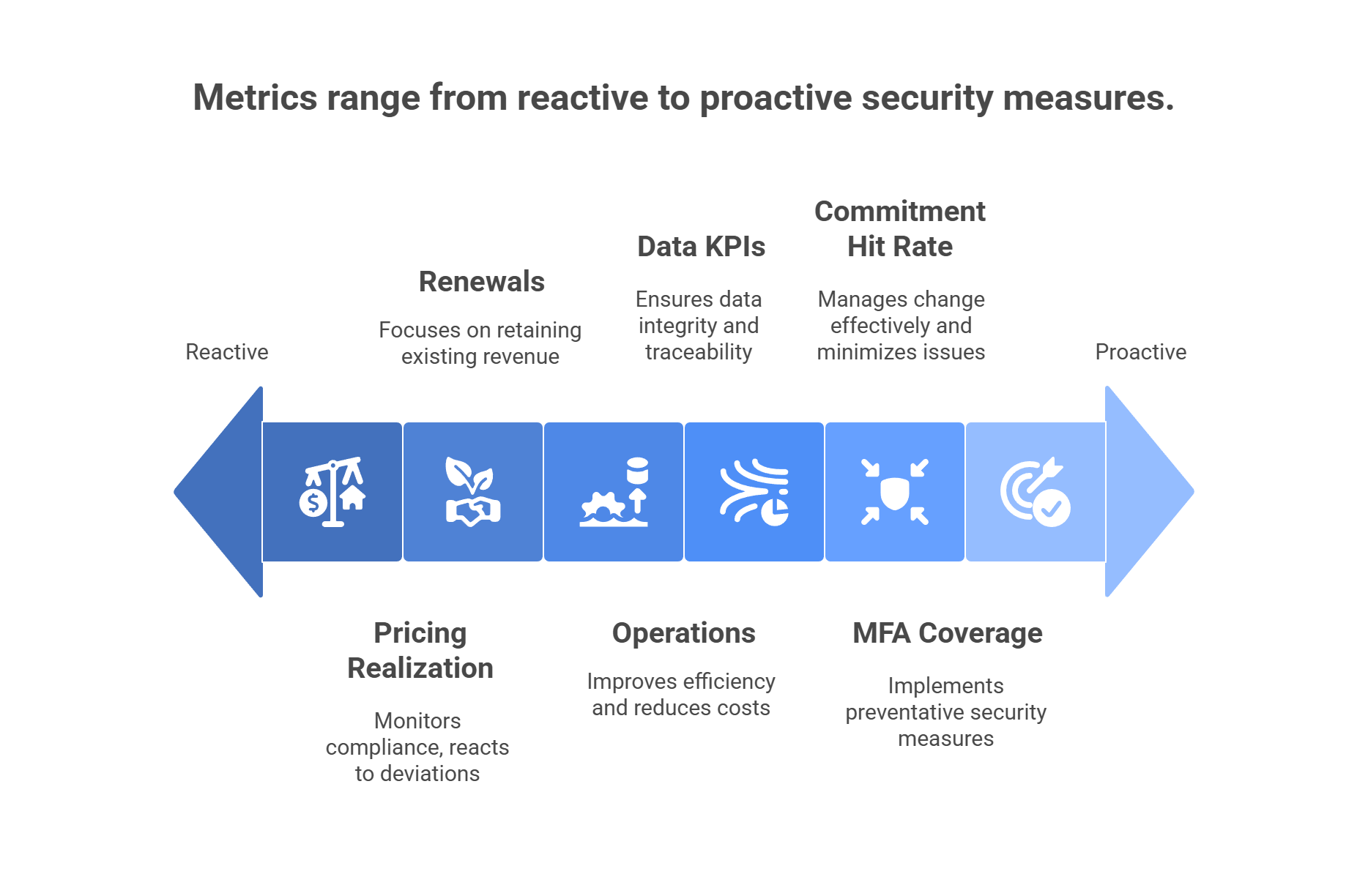
4. Metrics that matter (define, then secure)
5. Reproducibility standard (avoid disputes)
-
Store the exact query or script for each KPI.
-
Timestamp every export; include “as-of” dates on charts.
-
Provide a small sample dataset so a buyer can reproduce numbers in 30 minutes.
-
Archive monthly binders to an immutable folder; do not overwrite history.
6. Independent validation (when to use it)
-
Use third-party checks for security posture, data lineage audits, and model assumptions where credibility will be questioned.
-
Keep validations short, scoped, and tied to specific buyer risks.
7. Narrative that travels
-
Tell a risk story, not a risk list: item, mitigation, measurable effect.
-
Show before/after with dates, owners, and operating artifacts.
-
Emphasize routines that survive personnel changes (scripts, cadences, controls).
8. Common failure modes
-
“Digital” described as a project list without measured effects.
-
Hand-built dashboards with hidden manual steps; no lineage.
-
Security claims without access inventories or drill evidence.
-
Change cadence that exists in slides but not in issue logs.
-
Monthly packages that drift; no immutable archive.
9. Buyer Q&A rehearsal (sample)
-
Show me discount control. Open CPQ rules; show overrides with expiry and reason codes.
-
Rerun gross margin by family for last quarter. Execute the saved script; reconcile to the ledger.
-
Prove inventory health. Show turns, slow-moving actions, and policy results with dated evidence.
-
Test resilience. Produce the most recent incident drill log and follow-up actions.
10. One-page checklist
-
Evidence pack index with owners and update dates.
-
12-month KPI → P&L reconciliation workbook.
-
CPQ rule exports and override log.
-
CTS model with validation notes and policy outcomes.
-
Security posture summary with certifications and drill logs.
-
PMO cadence artifacts with commitment hit rate.
-
Data room binder and monthly immutable archives.
VCII Note and Copyright
TVC Next embeds Exit-Back design from day one. Digital proof is produced by routines—pricing rules, data lineage, operational controls, security drills, and PMO discipline—not by one-off projects. Package the routines, and the multiple follows.
Copyright © 2025 VCII, Meritrium Corp. All rights reserved.
We have many great affordable courses waiting for you!
Stay connected with news and updates!
Join our mailing list to receive the latest news and updates from our team.
Don't worry, your information will not be shared.
We hate SPAM. We will never sell your information, for any reason.